Teleworkers need to be protected!
The need to protect teleworkers CANNOT be overstated?
All employers have a responsibility to provide a safe and secure working environment for their employees.
The same goes for protecting teleworkers against cyberthreats in these turbulent times we live in right now.
And let’s face it, it goes without saying that, it is to the benefit of all employers to do so.


The COVID-19 pandemic has changed the world for everyone
It's even more so when it comes to office workers. Many of whom are now, and for the foreseeable future, working from home.
Although working from home as it's benefits such as being able to sleep a little longer, dressing casually, enjoying homemade lunches and not being stuck in traffic for hours, just to name a few, it also presents IT managers with challenges. One of which being cybersecurity.
Teleworking during the pandemic
Hackers are smart!
We need to protect ourselves against them!

Although there are companies that provide their employees with computers (mainly laptops), many telecommuters use their personal systems.
And even if your employees do use systems that were provided by their employer, who’s to say they don’t use those same systems for personal things?
Therein lies the problem for IT professionals!
These days, everyone is glued to the news and / or surfing the web to find out what’s happening, what governments are doing to help their citizens and, what are the latest rules and regulations to follow in order to stay safe.
Hackers are smart! They know that and are taking full advantage of it!
Every time you visit a site and fill-out some information requested in an on-line form, there’s a chance hackers can get all or parts of that information. The easiest of which is email addresses.
But that’s only one example. As it stands, there’s a new scam based on the COVID-19 crisis popping up daily

Beware of unsolicited emails (i.e.: email scams)
One that’s very popular with hackers these days is impersonating legitimate bodies, such as governments as well as health and safety organizations like the UN’s World Health Organization (WHO), the US’ Center for Disease Control and Prevention (CDC), Canada’s Public Health Agency and many others, in order to gain users’ trust and get them to open malicious emails.
And even though many governments and organizations have issued warnings, many people still fall prey to these scams.
Working from home gives you more time to relax and sometimes, that time is used to surf the net, catch up on work and personal emails. Whether you’re using your personal computer or one that was supplied by your employer, always be careful when receiving unsolicited emails.
Unsolicited emails often come from hackers looking to gain your trust and reveal private information about yourself as well as infect your systems and home network with malware!
Whether you’re using your personal system or one that was provided to you by your employer, when connecting that system to your own personal resources such as a home network, this is something no IT professional can control. It’s your responsibility to exercise caution as you’re the only one with full control over those resources!
If one of your home systems gets infected, it’s only a matter of time before the rest are.
To make matters worse, if you remotely access your company’s system, depending on the IT security measures your employer has in place, there’s a chance you can infect those as well! If that happens, the repercussions can be quite severe!
Consequences of opening unsolicited emails
Here are a couple examples of dangerous unsolicited emails. Can you spot the problems?

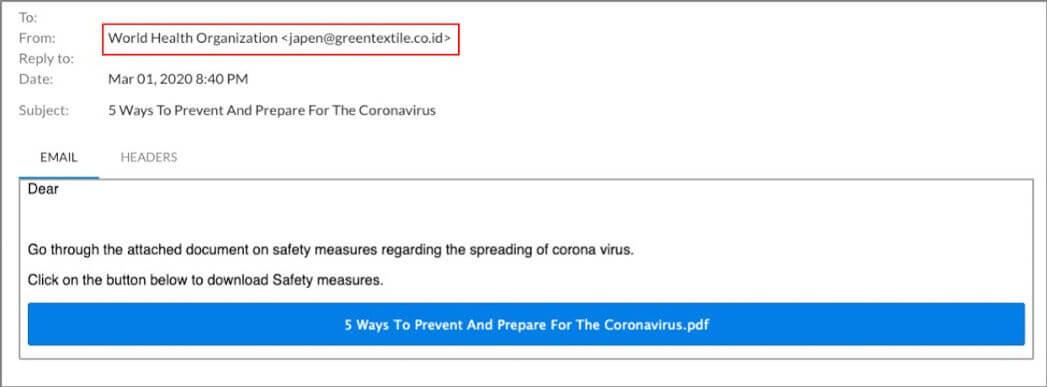
The types of attacks shown in the above images can have serious consequences such as:
- Infecting the device you opened the email on with malware and spreading it throughout your other devices ( local and remote) on the network.
- Stealing login credentials by way of phishing sites or other phishing methods.
- Collecting private information such as credit card details, through donations done on a fake charity website.
Hackers often use impersonation tactics to trick users into thinking their emails are legitimate. These tactics include malicious links in the body of the email and / or malicious attachments.
- When clicking on those links your often sent to a website where you’re prompted to enter personal information hackers will collect.
- When opening the attachment, malware is installed on your computer or other device being used.
- Malware that can than spread to all other connected devices.

Teleworkers at risk of falling prey to phishing attacks!
When working at the office, IT security mechanisms and resources are in place to protect the company's assets against hacking attempts.
When working remotely from home, the same is not always true!

Protecting all employees from cyberthreats
Protecting employees CANNOT be limited to ONLY when they are in the office!
Protecting teleworkers from hackers, phishing scams and other types of cyberattacks is just as important as protecting office workers.
When working from home, users are more likely to open emails they believe come from a legitimate source.
This is why protecting teleworkers from the various and ever-present cyberthreats is a must!
Mitigating the threat level
What can employers do to manage and mitigate the threat level email scams can cause?
Be it for office workers or teleworkers, it all starts with education. Educate your employees on cybersecurity and cyberthreats.
This is especially needed in these chaotic times we currently live in and, in the long run, this will help protect both your employees and your corporate assets.
Educating workers on cybersecurity is essential!
- Don’t click on any links found in emails coming from sources you don’t know, as these links can send you to malicious websites.
- Be wary of any emails coming in from governmental health and safety agencies. Instead, go directly to these organizations’ websites for the latest information.
- If you receive emails from co-workers or company executives updating you on things, double-check their emails to make sure it’s really coming from them. Better yet, pick up the phone and call them directly to confirm they are indeed the ones who sent the email.
- Never give out any personal information, login credential or make any payments in response to an email.
- All email scams received on your work address should be reported to the IT management. If it comes in on your personal address, classify them as spam and add the email address to your blacklist.
- Remind your employees to have up-to-date and reliable antivirus, anti-phishing and anti-malware software, installed on their devices.
- If the computer you use to work remotely is provided from the company, your employer’s IT department can provide those
- Make sure that upon them becoming available, all security updates, upgrades and patches are immediately installed
Protect your data and employees from cybercriminals
As previously mentioned, the above applies whether you’re using your own personal devices or systems provided by your employers.
It doesn’t stop there, however. For companies to protect their teleworkers, the following is also highly recommended
- Have content filtering security solutions in place to filter malicious emails, inappropriate content and malicious websites.
- Having a local backup solution in place, complemented by cloud backup services.
- Have a VPN solution in place and provide VPN clients to the employees, so your remote workers can securely connect to the corporate network and securely communicate as well as exchange files and data safely.


